Anyway, I tend to use it for testing WEP encrypted networks (purely for educational purposes, mind) and I've learned how to do it using the command line. Then someone pointed out that a utility called Spoonwep will do the job using a simple GUI.
So I gave it a go. You won't learn much from it, I would strongly recommend you learn the command line way (which is a lot more powerful), but it is a bit of a time saver.
Here's how to do it:
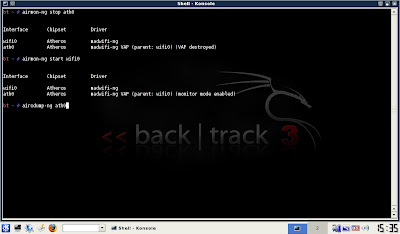
01) Open a terminal:
airmon-ng stop ath0
02) Next:
airmon-ng start wifi0
03) Next:
airodump-ng ath0
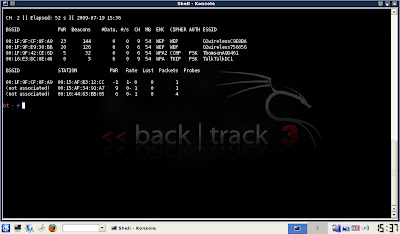
04) Choose the AccessPoint(AP) you want to hack and remember the channel number. The AP will need to have a PWR rating of above 20 to have any chance of this working.
05) Hit CTRL+C to stop
06) Then copy the AP MAC address
07) In the same terminal:
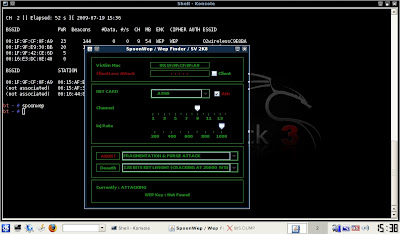
spoonwep
08) In Victim MAC, paste the AP MAC Address
09) Choose your network card. On the EeePC 701 and 900 it's Ath0
10) Set the AP Channel Number
11) Set the Injection Rate to maximum
12) Use Fragmentation and Forge Attack
13) Use 128 Bits Key Length
14) Click launch. It does take some time, usually between ten and twenty minutes. Just be patient.
15) If it works, the key will appear as a string of characters punctuated by colons. Remove the colons and your key is what remains.
Example: 12:34:56:78:90 should be read as 1234567890.
Here's some screen shots of Spoonwep in action on my brother's network:
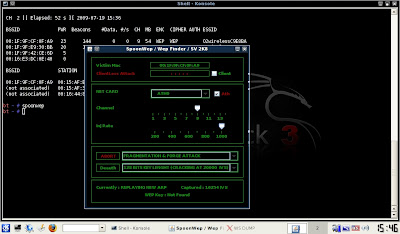
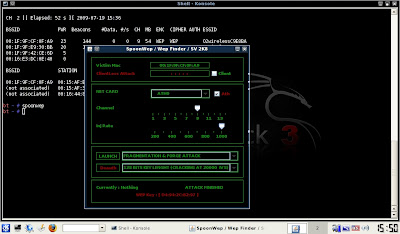
Not bad, eh? Fifteen minutes to crack my brother's WEP key.
Wasn't he surprised!! Needless to say he's changed his encryption to WPA...

No comments:
Post a Comment